New Guide: Protect Your Business from Payroll Leakage & Legal Risk in 2026
CONTROL ACCESS, PROTECT WHAT MATTERS
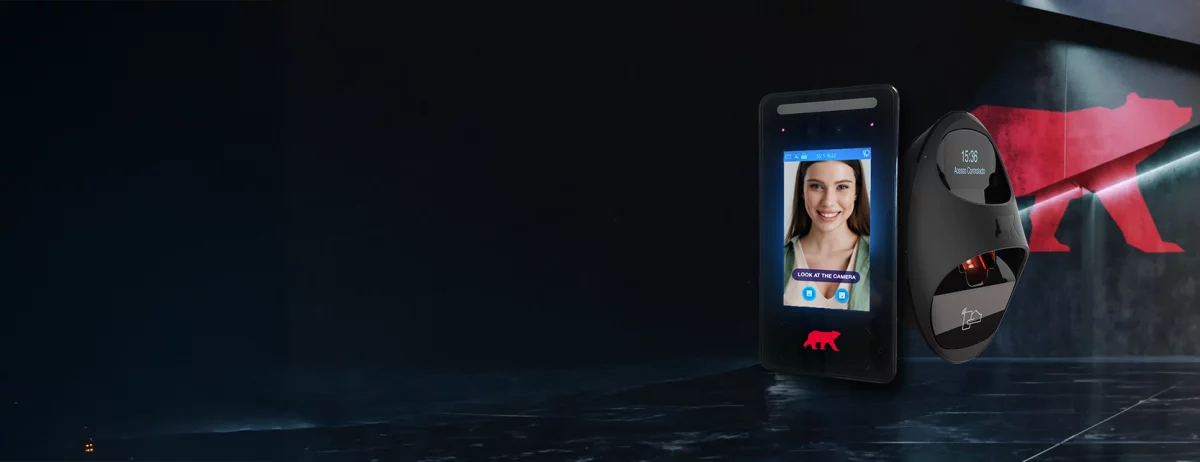
Eliminate keycards & PINs — Secure your site with next-gen biometric technology.
Secure your premises with industry leading technology that identifies who is accessing your site, not just when.
Almas Industries have developed, manufactured, installed serviced and maintained biometric access solutions throughout Europe for decades.
Choose biometric experts when future-proofing your company’s security.
Quick, contactless identification with advanced AI-based facial recognition.
Perfect for high-traffic, hygienic, and secure environments.
Proven and reliable, our fingerprint readers offer secure access management that’s ideal for staff entry points and restricted zones.
Vein recognition scans the unique patterns inside a user’s finger or hand. Highly secure and unaffected by dirt, skin damage, or environmental conditions.
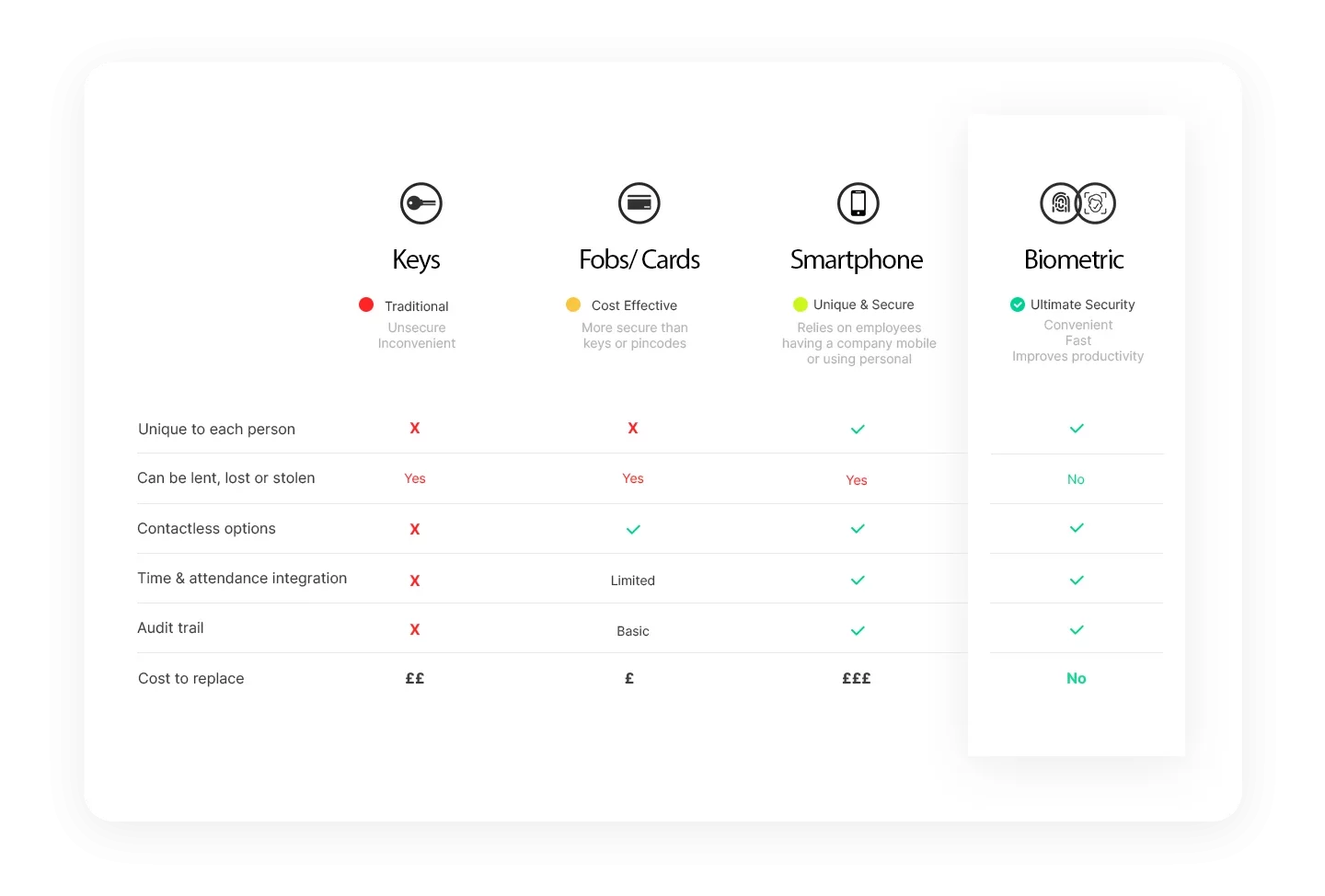
How do biometric technologies stack up against traditional access control systems?
Looking to upgrade your existing access system?

Hear from our customer Hollybank Trust how biometric access and 360 security has improved security and positively benefitted their residents and care givers.
Almas Industries were protecting UK & Irish businesses with biometric technologies long before Apple adopted it on smartphones! We work with businesses from 5 to 50,000 employees across Europe and manufacture our own fingerprint readers and develop our own access control software.


CONSULTATION & SPECIFICATION
Advice on the right biometric access control system; tailored to your site, the flow of people and vehicles, the hours of operation, level of security required and user experience.
![]()
EXPERT PROJECT MANAGEMENT
End to end support. Professional installation by our own engineers to PSA/ SSAIB standards, site survey plan, on-site training and comprehensive user guides.
![]()
COMPLIANCE & GDPR
A privacy first approach that’s fully GDPR compliant. Support with clear effective comms for your users, guidance and PIA templates to help you stay compliant with data protection laws. Robust cyber security.
![]()
SUPPORT & TECHNICAL SERVICES
Post-installation, our commitment continues with further training, proactive intelligent system health monitoring, and a robust hardware guarantee, ensuring your peace of mind.
“Have used Almas for since July 2008. Service, price and aftercare has always been top shelf. Five 🌟 all the way.” Lunarium Property Holdings Ltd.
“Bishop Vesey’s Grammar School has been working with Almas for nearly 15 Years. They have support the schools growth and offer excellent advice, support and overall service. I would recommend to any organisation.”
"Excellent support, latest technology, innovative. We have CCTV and Facial Recognition systems installed securing our premises to the highest standard. "
Read More"Day Care at Saint Martins is protected by biometric access control and CCTV from Almas Industries"
Read More""We've found the workmanship of the technicians to be of the highest quality and Almas' advice has saved us money in terms of on-site security. Almas' responsiveness to our changing needs allows us to scale our security solutions as required, as we continue to grow" Stephen Tedstone, Production Director"
Read More"We’ve been using innDex at Ilford Station over the past 6 months and the efficiencies have shown to be outstanding."
Read More"When they came out to demo the 360 system, we knew that that system was the system that we wanted to utilise."
Read MoreSpeak to our Security Experts today.
We are here to help.
Get A Free Security Consultation & Quote
Or call us on 0808 109 3412 (UK) or 01 68 333 68 (IRE)
From data security to cost – here are the questions we are most often asked about Biometric Access Control.
If you’ve any more questions please do drop us a line and we will be happy to answer them.
What is biometric access control?
 Biometric access control is a type of access control system that uses an individual’s unique physiological or behavioural characteristics to confirm their identity and grant access to restricted areas.
Biometric access control is a type of access control system that uses an individual’s unique physiological or behavioural characteristics to confirm their identity and grant access to restricted areas.
Biometric access control systems, as opposed to traditional access control systems that rely on key cards, fobs, or codes, use an individual’s unique biological features for authentication, such as fingerprints, facial recognition, iris or retina scans, voice recognition, or even hand geometry.
The primary benefit of biometric access control systems is the increased security they provide. Because biometric characteristics are unique to each individual, these credentials are extremely difficult to duplicate, forge, or share, making them a more secure option than key cards or codes, which can be lost, stolen, or shared.
Because of their enhanced security, convenience, and ability to quickly and accurately authenticate users, biometric access control systems are becoming increasingly popular in a variety of settings, including offices, government facilities, research labs, and data centres.
How much do biometric access control systems cost?
We know you want a price straight away! But, we want to give you an accurate price and to do that, we need to check out many things on site including (but not limited to):
If you’d like a rough idea of how much systems cost, you can read our comprehensive article on how much access control systems cost here
Are biometric access control systems expensive?
Biometric access control systems certainly come at a cost, and this will vary greatly depending on the manufacturer, the quality of the system, and the related software.
On a sliding scale, fingerprint scanners are now an affordable solution, as are facial reader (but be careful with quality of both of these). Venal and iris scanners are more expensive, and generally reserved for high security requirements. Voice recognition scanners are rare and not generally used as a form of commercial access control (yet!)
These biometric systems represent a sophisticated form of technology, and whilst there are more affordable options available, it’s critical to bear in mind that you should not compromise the security of the system and the data it manages for the sake of cost savings.
Are all biometric access control readers the same?
No, not all biometric readers are the same. Biometric readers can be classified based on the type of biometric data they collect and process. Here are some common types of biometric readers:
These are the most common type of biometric readers. They capture the patterns of ridges and valleys in a fingerprint to create a map that is used for identification.
These systems use cameras to capture facial features from a photo or video. They then use algorithms to compare the captured facial features with the ones in the database.
These scanners capture the pattern of veins under the skin by bouncing infrared light through the dermis. This is often done on the back of the hand or the finger, your highly complex and unique venal network is then turned into a biometric template. Vein patterns are unique and remain stable over time.
These biometric readers identify the unique patterns in irises, which are the coloured area around your pupil.
It’s non-contact and easy to use. Using vocal verification for access control is a relatively new concept. There is a different between speech recognition – that is being able to interpret what someone is saying, and vocal verification which is using what someone is saying to identify that they are who they claim to be.
Each type of biometric reader offers different advantages in terms of user acceptance and suitability for different environments or applications. Read our leading article on whether all biometric readers are the same here
Are biometric access control readers waterproof?
Yes, most biometric access control readers are designed to be waterproof and robust to withstand various environmental conditions. They typically come with an Ingress Protection (IP) rating, which is a standard that denotes the degree of protection provided against the intrusion of solids and liquids.
For instance, Almas’ facial recognition and fingerprint readers mentioned have an IP rating of 65.
This means they are dust-tight and protected against low-pressure water jets from any direction, comparable to rain or a sprinkler. However, they are not designed to withstand extremely high-pressure water streams, like those from a fireman’s hose, which could potentially cause damage.
Despite this, under most normal and even challenging conditions, such as inclement weather, these readers prove to be robust, reliable, and tamper-proof. Their design ensures they can provide consistent performance and maintain the security integrity of the system, making them suitable for a variety of installation environments.
Right equipment for the right location
As with all security equipment, it’s important to consider the specific environmental conditions of your site when choosing and installing your biometric readers.
Can my biometric data be stolen?
Some systems take a picture of the biometric attribute and save it within the software, some softwares encrypt and convert this data so it’s stored as code rather than an image. It’s important to investigate which approach your potential supplier uses because the second is much more secure than the first one!
What is absolutely vital is that any business contemplating adopting a biometric entry system must conduct a privacy impact assessment and comply with GDPR regulations.
Read all about biometric data storage in access control systems here
How could biometric access control work for event management?
Pre-enrolment of visitors, staff or VIPs before events can streamline processes and reduce long queues, thereby improving your users’ experience and reduce ticket touting or staffing substitution.
Read more on biometric technology in the events industry and how it can help reduce the challenges faced here.
Can someone take a picture of my face or copy my fingerprint and use it?
Our biometric readers using anti-phishing technology which can distinguish whether the credential presented to the reader is a real person or a photo.
Are biometric solutions complicated?
Complicated and clever technology but easy to use! Almas’ approach ensures that your access control system is set up to your needs upon installation and we are always on hand to help if key users move on and additional training is needed.
We will work with IT departments to make sure your infrastructure is set up for your new system and liaise with them regarding GDPR considerations so you know all your data is safe and sound.
Can biometric readers be installed anywhere?
They can be installed almost anywhere.. We always conduct a site survey before giving a quote because we want to be certain we’ve given you an accurate price.
Various factors such as building construction, whether it’s listed, asbestos and more all factor in. Generally we can install pretty much anywhere but if you want us to put a reader on an ocean of glass we may have to say no!
How many users can be added to the system?
We have a number of biometric solutions, but each device can register at least 3,000 users (up to 50,000 on some).
What happens if someone can't use their fingerprint or face? Or they don't want to?
Multi-modal options like PINs or cards can be used as a backup. Ultimately when considering whether to implement a biometric system, you must communicate with your teams and if they don’t want to use their face or finger, then you must give them an alternative way of clocking in or gaining access.
Will we all end up having to use biometric identification?
Biometric identification and authentication are thorny subjects. In an increasingly digital world we are sharing more data than ever on line and as criminals get more sophisticated, so do checks to protect us!
With the advent of GDPR in 2018, the issue of data privacy, especially online was addressed. We believe that the benefits of biometric systems should be weighed against data privacy and all systems should be designed from a privacy first standpoint.
We wrote an article back in 2019 about this and we still think it’s interesting! You can read more about whether biometrics will see the end of identity documentation here
What is the biggest benefit of biometric access control?
The biggest benefit of biometric access control is enhanced security. Since biometric identifiers are unique to each person and difficult to duplicate or forge, they offer greater protection than traditional methods like cards or codes. This makes them ideal for high-security environments such as offices, data centres, research labs, and government facilities.
How much do biometric access control systems cost?
The cost of a biometric access control system depends on multiple site-specific factors, such as internet and power availability, wall and ceiling construction, listed building status, asbestos, emergency exits, environmental conditions, installation time, and integration with other systems like CCTV or fire alarms. Because of these variables, a site survey is needed to provide an accurate quote. For a rough guide to pricing, see our detailed article on access control system costs
Are all biometric access control readers the same?
No, not all biometric readers are the same. Biometric readers can be classified based on the type of biometric data and the way they collect and process.
Are biometric access control systems expensive?
The cost of biometric access control systems varies depending on the technology and quality. Fingerprint and facial recognition scanners are generally affordable options, while more advanced solutions like vein and iris scanners are more expensive and used for high-security applications. Although prices differ, it’s important not to compromise on system quality or data security to save costs.
Are biometric access control readers waterproof?
Yes, many biometric access control readers are designed to be waterproof and durable, with an Ingress Protection (IP) rating to show their resistance to dust and water. For example, readers with an IP65 rating are dust-tight and protected against low-pressure water jets, making them suitable for outdoor use in rain or sprinklers. While they cannot withstand extreme high-pressure water, they remain reliable, tamper-proof, and secure in most environments. It’s always important to match the equipment to the specific conditions of your site.